John the ripper guide Hawkes Bay
John the Ripper 1.9.0 Download TechSpot Jun 09, 2018 · 1 Comment → Beginners Guide for John the Ripper (Part 2) Krishanu February 17, 2019 at 5:52 am. Raj, Great blog post and it helped me learn. However, the 7z to john hasn’t worked for me. it always errors out with something weird. For example recently i was trying to do a ctf and that gave me a password encoded 7z.
Johnny GUI for John the Ripper [Openwall Community Wiki]
John the Ripper Penetration Testing Tools. John the Ripper usage examples. These examples are to give you some tips on what John's features can be used for. Command line. 1. First, you need to get a copy of your password file. If your system uses shadow passwords, you may use John's "unshadow" utility to …, John the Ripper is one of the most popular password cracking tools available that can run on Windows, Linux and Mac OS X. Just download the Windows binaries of John the Ripper, and unzip it. Open a Command Prompt and change into the directory where John the Ripper is located, then type: john --format=LM d:\hash.txt.
Dec 27, 2001 · Directed by John Eyres. With A.J. Cook, Bruce Payne, Ryan Northcott, Claire Keim. A massacre survivor (A.J. Cook) studies serial killers under a famous expert (Bruce Payne), but her classmates soon start dying at the hands of a Jack the Ripper copycat. Dec 27, 2001 · Directed by John Eyres. With A.J. Cook, Bruce Payne, Ryan Northcott, Claire Keim. A massacre survivor (A.J. Cook) studies serial killers under a famous expert (Bruce Payne), but her classmates soon start dying at the hands of a Jack the Ripper copycat.
password generator and all-around cracking tool. John the Ripper · Category:John the Ripper. Installing John the Ripper on Kali 2.0: Kali 2.0/John the Ripper Testing John: John the Ripper/Benchmarking Using John on /etc/shadow files: John the Ripper/Shadow File. Password generation using rules and modes: John the Ripper/Password Generation Installing some useful password rules: John the Below a quick step-by-step guide on how to install and run the latest version of John the Ripper across several system using OpenMPI framework taking advantage of NFS to share common files. All this using Kali Linux. By creating this small environment we foster the knowledge and promote learning about different tools and techniques. The…
Johnny is the cross-platform Open Source GUI frontend for the popular password cracker John the Ripper. It was originally proposed and designed by Shinnok in draft, version 1.0 implementation was achieved by Aleksey Cherepanov as part of GSoC 2012 and Mathieu Laprise took Johnny further towards 2.0 and beyond as part of GSoC 2015. We know the importance of John the ripper in penetration testing, as it is quite popular among password cracking tool. In this article, we are introducing the John the ripper and its various usage for beginners. What is John the Ripper? John the Ripper is a free password cracking software tool developed by Openwall. Originally developed for Unix Operating Systems but later on developed for
Feb 18, 2018 · Hey guys! HackerSploit here back again with another video, in this video, we will be looking at Linux and encrypted password cracking with John the Ripper. J... John the Ripper is one of the most popular password cracking tools available that can run on Windows, Linux and Mac OS X. Just download the Windows binaries of John the Ripper, and unzip it. Open a Command Prompt and change into the directory where John the Ripper is located, then type: john --format=LM d:\hash.txt
Lab 8: Using John the Ripper to Crack Linux Passwords 3 This work by the National Information Security and Geospatial Technologies Consortium (NISGTC), and except where otherwise noted, is licensed under the Creative Commons Attribution 3.0 Unported License. Introduction We know the importance of John the ripper in penetration testing, as it is quite popular among password cracking tool. In this article, we are introducing the John the ripper and its various usage for beginners. What is John the Ripper? John the Ripper is a free password cracking software tool developed by Openwall. Originally developed for Unix Operating Systems but later on developed for
Jun 05, 2018 · We know the importance of John the ripper in penetration testing, as it is quite popular among password cracking tool. In this article, we are introducing John the ripper and its various usage for beginners. What is John the Ripper? John the Ripper is a free password cracking software tool developed by Openwall. Originally developed... Continue reading → John the Ripper usage examples. These examples are to give you some tips on what John's features can be used for. Command line. 1. First, you need to get a copy of your password file. If your system uses shadow passwords, you may use John's "unshadow" utility to …
Below a quick step-by-step guide on how to install and run the latest version of John the Ripper across several system using OpenMPI framework taking advantage of NFS to share common files. All this using Kali Linux. By creating this small environment we foster the knowledge and promote learning about different tools and techniques. The… John the Ripper usage examples. These examples are to give you some tips on what John's features can be used for. Command line. 1. First, you need to get a copy of your password file. If your system uses shadow passwords, you may use John's "unshadow" utility to …
Apr 15, 2015 · I have a video showing how to use oclHashcat to crack PDF passwords, but I was also asked how to do this with John The Ripper on Windows. It's not difficult. Download the latest jumbo edition john-the-ripper-v1.8.0-jumbo-1-win-32.7z from the custom builds page. Decompress this version. Download the previous jumbo edition John the Ripper 1.7.9-jumbo-5 (Windows… John The Ripper: Beginner's Tutorial John The Ripper: Beginner's Tutorial. In previous post on John The Ripper we saw how to compile it for Linux and UNIX boxes. Now its time to begin out password cracking journey with John The Ripper.
Jul 15, 2013 · Brute Forcing Passwords with John the Ripper Objective. To configure John the Ripper to brute force 8 character case sensitive passwords that contain alphabet and numeric characters. By default John is not capable of brute forcing case sensitive alpha-numeric passwords. John uses character sets contained in .chr files. Jun 09, 2018 · 1 Comment → Beginners Guide for John the Ripper (Part 2) Krishanu February 17, 2019 at 5:52 am. Raj, Great blog post and it helped me learn. However, the 7z to john hasn’t worked for me. it always errors out with something weird. For example recently i was trying to do a ctf and that gave me a password encoded 7z.
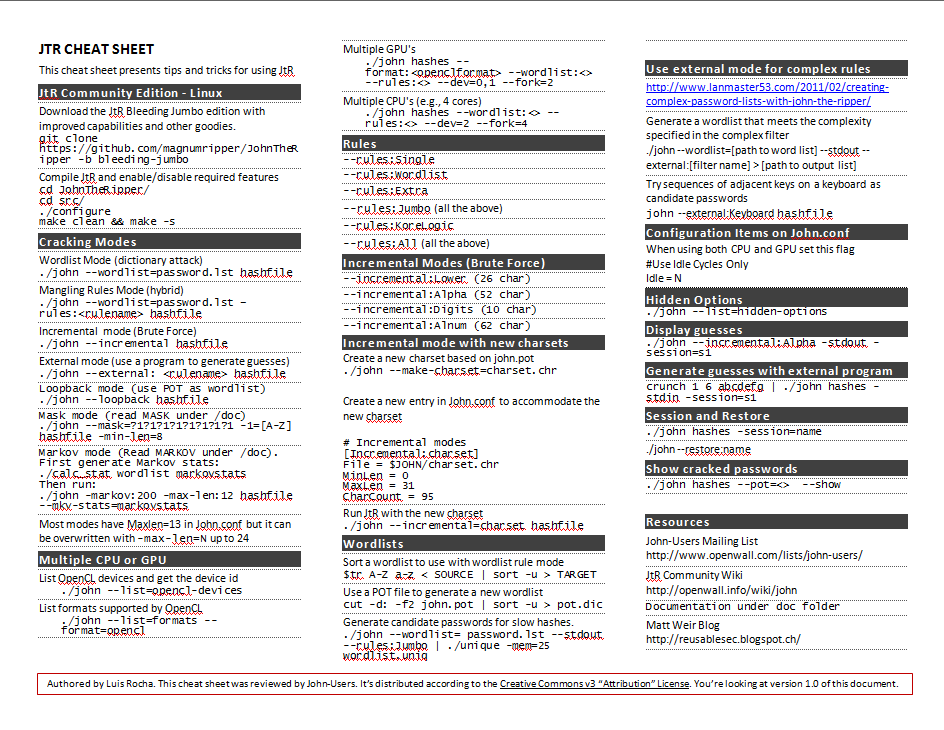
Dec 27, 2001 · Directed by John Eyres. With A.J. Cook, Bruce Payne, Ryan Northcott, Claire Keim. A massacre survivor (A.J. Cook) studies serial killers under a famous expert (Bruce Payne), but her classmates soon start dying at the hands of a Jack the Ripper copycat. Jul 12, 2015 · Home » Tutorials » John The Ripper – Kali Linux Tips and Cheats. Tutorials. John The Ripper – Kali Linux Tips and Cheats. by admin Published July 12, 2015. I created a quick reference guide for John the Ripper. Useful for those starting in order to get familiar with the command line. Print it, laminate it and start practicing your
May 20, 2019 · Download John the Ripper. John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, and OpenVMS. In John The Ripper we execute a brute force attack like so: This command string ‘John-386 hash.txt’, where hash.txt is where the hash is stored, will run a basic Brute Force attack on the hash. Luckily for us we can make this command much more specific with some of the following commands:
John the Ripper documentation openwall.com

John the Ripper GUI Frontend Johnny CyberPunk. May 21, 2019 · Hi I have a problem with John the ripper: Version :John the Ripper 1.8.0-jumbo-1 Windows XP SP3/ Windows 7 I tried to decrypt a winrar file but i..., Feb 08, 2017 · Noob's Guide To Bitcoin Mining - Super Easy & Simple - Duration: 11:37. UFD Tech Recommended for you. 11:37. How to install and use John The Ripper MiRoCo Tech. Loading....
PDF Password Cracking With John The Ripper Didier Stevens
Cracking password in Kali Linux using John the Ripper. John The Ripper: Beginner's Tutorial John The Ripper: Beginner's Tutorial. In previous post on John The Ripper we saw how to compile it for Linux and UNIX boxes. Now its time to begin out password cracking journey with John The Ripper. https://fr.m.wikipedia.org/wiki/Jack_l%27%C3%89ventreur_(t%C3%A9l%C3%A9film,_1988) Feb 08, 2017 · Noob's Guide To Bitcoin Mining - Super Easy & Simple - Duration: 11:37. UFD Tech Recommended for you. 11:37. How to install and use John The Ripper MiRoCo Tech. Loading....

This is the full-text of the original E-Book Jack the Ripper: A Suspect Guide by Christopher J. Morley. It is unedited - any errors or omissions rest with the author. Our thanks go out to Christopher for giving us permission to publish his E-book on Casebook: Jack the Ripper. John The Ripper: Beginner's Tutorial John The Ripper: Beginner's Tutorial. In previous post on John The Ripper we saw how to compile it for Linux and UNIX boxes. Now its time to begin out password cracking journey with John The Ripper.
Feb 18, 2018 · Hey guys! HackerSploit here back again with another video, in this video, we will be looking at Linux and encrypted password cracking with John the Ripper. J... John the Ripper password cracking tool - How to use Step by step guide IT Security. I will give 1min theory lec on this first :P John the Ripper is free open source password cracking tool for Linux , Unix and Mac OS X . A windows version is also available.
John the Ripper. Next we’ll need the cracking tool itself. If you’re using Kali Linux, this tool is already installed. Download John the Ripper here. In my case I’m going to download the free version John the Ripper 1.8.0 (sources, tar.gz, 5.2 MB). Once downloaded, extract it with the following linux command: john Package Description. John the Ripper is designed to be both feature-rich and fast. It combines several cracking modes in one program and is fully configurable for your particular needs (you can even define a custom cracking mode using the built-in compiler supporting a subset of C).
Jul 12, 2015 · Home » Tutorials » John The Ripper – Kali Linux Tips and Cheats. Tutorials. John The Ripper – Kali Linux Tips and Cheats. by admin Published July 12, 2015. I created a quick reference guide for John the Ripper. Useful for those starting in order to get familiar with the command line. Print it, laminate it and start practicing your The 2730 is a combination ripper that integrates four operational areas into one system. These four areas consist of disk blades, ripper shanks, rear closing disks, and finishing attachments. The ability to quickly and conveniently customize these components independently offers reduced cost of operation and maximum productivity.
Jan 26, 2017 · Although projects like Hashcat have grown in popularity, John the Ripper still has its place for cracking passwords. One of the advantages of using John is that you don’t necessarily need Dec 01, 2010 · By Thomas Wilhelm, ISSMP, CISSP, SCSECA, SCNA Many people are familiar with John the Ripper (JTR), a tool used to conduct brute force attacks against local passwords. The application itself is not difficult to understand or run… it is as simple as pointing JTR to a file containing encrypted hashes and leave it alone. In a professional penetration test, we don’t […]
Jack the Ripper: A Suspect Guide This text is from the E-book Jack the Ripper: A Suspect Guide by Christopher J. Morley (2005). Click here to return to the table of contents. The text is unedited, and any errors or omissions rest with the author. Apr 15, 2015 · I have a video showing how to use oclHashcat to crack PDF passwords, but I was also asked how to do this with John The Ripper on Windows. It's not difficult. Download the latest jumbo edition john-the-ripper-v1.8.0-jumbo-1-win-32.7z from the custom builds page. Decompress this version. Download the previous jumbo edition John the Ripper 1.7.9-jumbo-5 (Windows…
Jul 15, 2013 · Brute Forcing Passwords with John the Ripper Objective. To configure John the Ripper to brute force 8 character case sensitive passwords that contain alphabet and numeric characters. By default John is not capable of brute forcing case sensitive alpha-numeric passwords. John uses character sets contained in .chr files. In John The Ripper we execute a brute force attack like so: This command string ‘John-386 hash.txt’, where hash.txt is where the hash is stored, will run a basic Brute Force attack on the hash. Luckily for us we can make this command much more specific with some of the following commands:
John the Ripper is designed to be both feature-rich and fast. It combines several cracking modes in one program and is fully configurable for your particular needs (you can even define a custom cracking mode using the built-in compiler supporting a subset of C). Also, John is available for several different platforms which enables you to use Lab 8: Using John the Ripper to Crack Linux Passwords 3 This work by the National Information Security and Geospatial Technologies Consortium (NISGTC), and except where otherwise noted, is licensed under the Creative Commons Attribution 3.0 Unported License. Introduction
Jun 09, 2018 · 1 Comment → Beginners Guide for John the Ripper (Part 2) Krishanu February 17, 2019 at 5:52 am. Raj, Great blog post and it helped me learn. However, the 7z to john hasn’t worked for me. it always errors out with something weird. For example recently i was trying to do a ctf and that gave me a password encoded 7z. May 12, 2017 · Here is how to crack a ZIP password with John the Ripper on Windows: First you generate the hash with zip2john: Then you run john: In this example, I use a specific pot file (the cracked password list). Quickpost info
John the Ripper is a free password cracking software tool. Initially developed for the Unix operating system, it now runs on fifteen different platforms (eleven of which are architecture-specific versions of Unix, DOS, Win32, BeOS, and OpenVMS). May 20, 2019 · Download John the Ripper. John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, and OpenVMS.
Feb 08, 2017 · Noob's Guide To Bitcoin Mining - Super Easy & Simple - Duration: 11:37. UFD Tech Recommended for you. 11:37. How to install and use John The Ripper MiRoCo Tech. Loading... May 20, 2019 · Download John the Ripper. John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, and OpenVMS.
k l) 117"% b"% zzzzzzzzzz zzzzzzzzzz b b"" d b"# b"% b"$ b"# b l 3 3 b"$ b"# b"! b b"$ zzzzzzzzz full? zzzzzzzzzb l"$ b."# b"# b b"# zzzzzzzzz ВЅ? zzzzzzzzz b l k l Guns and roses sweet child of mine tab pdf Tauranga Sweet Child O' Mine by Guns N' Roses tab with free online tab player. One accurate version. Recommended by The Wall Street Journal
Beginners Guide for John the Ripper (Part 1)

John the Ripper password cracking tool How to use Step. Jun 09, 2018 · 1 Comment → Beginners Guide for John the Ripper (Part 2) Krishanu February 17, 2019 at 5:52 am. Raj, Great blog post and it helped me learn. However, the 7z to john hasn’t worked for me. it always errors out with something weird. For example recently i was trying to do a ctf and that gave me a password encoded 7z., May 21, 2019 · Hi I have a problem with John the ripper: Version :John the Ripper 1.8.0-jumbo-1 Windows XP SP3/ Windows 7 I tried to decrypt a winrar file but i....
PDF Password Cracking With John The Ripper Didier Stevens
Build Your Own. Jul 21, 2015 · Johnny the open source cross-platform GUI frontend for John the Ripper, the popular password cracker, written in C++ using the Qt framework. Johnny’s aim is to automate and simplify the password cracking routine on the Desktop as well as add extra functionality like session management and easy hash/password management, on top of the immense capabilities and features offered by …, Aug 08, 2013 · John the ripper is a popular dictionary based password cracking tool. It uses a wordlist full of passwords and then tries to crack a given password hash using each of the password from the wordlist. In other words its called brute force password cracking and is ….
Jan 26, 2017 · Although projects like Hashcat have grown in popularity, John the Ripper still has its place for cracking passwords. One of the advantages of using John is that you don’t necessarily need This is the full-text of the original E-Book Jack the Ripper: A Suspect Guide by Christopher J. Morley. It is unedited - any errors or omissions rest with the author. Our thanks go out to Christopher for giving us permission to publish his E-book on Casebook: Jack the Ripper.
John the Ripper usage examples. These examples are to give you some tips on what John's features can be used for. Command line. 1. First, you need to get a copy of your password file. If your system uses shadow passwords, you may use John's "unshadow" utility to … John the Ripper. Next we’ll need the cracking tool itself. If you’re using Kali Linux, this tool is already installed. Download John the Ripper here. In my case I’m going to download the free version John the Ripper 1.8.0 (sources, tar.gz, 5.2 MB). Once downloaded, extract it with the following linux command:
John the Ripper (ou JTR, ou John) est un logiciel libre de cassage de mot de passe, John est l'un des craqueurs de mots de passe les plus populaires, car il. 1 manual pdf search engines guide directories internet david clark h10 13x manual Manual honda gyro x john platter guide owner's manual for the brain cod4. John The Ripper Manual Pdf Johnny is the cross-platform Open Source GUI frontend for the popular password cracker John the Ripper. It was originally proposed and designed by Shinnok in draft, version 1.0 implementation was achieved by Aleksey Cherepanov as part of GSoC 2012 and Mathieu Laprise took Johnny further towards 2.0 and beyond as part of GSoC 2015.
Apr 19, 2019 · John The Ripper Password Cracking Tool Free Download (2019 Edition) In this guide, we learned about the password cracking software named “John the Ripper“. This tool is totally free to download and very good for password hacking and cracking. As I said before you should download the original version of this software because there are many Jul 21, 2015 · Johnny the open source cross-platform GUI frontend for John the Ripper, the popular password cracker, written in C++ using the Qt framework. Johnny’s aim is to automate and simplify the password cracking routine on the Desktop as well as add extra functionality like session management and easy hash/password management, on top of the immense capabilities and features offered by …
Windows password cracking using John The Ripper. In this post I will show you how to crack Windows passwords using John The Ripper. John the Ripper is a fast password cracker, primarily for cracking Unix (shadow) passwords.Other than Unix-type encrypted passwords it also supports cracking Windows LM hashes and many more with open source contributed patches. Apr 15, 2015 · I have a video showing how to use oclHashcat to crack PDF passwords, but I was also asked how to do this with John The Ripper on Windows. It's not difficult. Download the latest jumbo edition john-the-ripper-v1.8.0-jumbo-1-win-32.7z from the custom builds page. Decompress this version. Download the previous jumbo edition John the Ripper 1.7.9-jumbo-5 (Windows…
John the Ripper is designed to be both feature-rich and fast. It combines several cracking modes in one program and is fully configurable for your particular needs (you can even define a custom cracking mode using the built-in compiler supporting a subset of C). Also, John is available for several different platforms which enables you to use This is the full-text of the original E-Book Jack the Ripper: A Suspect Guide by Christopher J. Morley. It is unedited - any errors or omissions rest with the author. Our thanks go out to Christopher for giving us permission to publish his E-book on Casebook: Jack the Ripper.
Windows password cracking using John The Ripper. In this post I will show you how to crack Windows passwords using John The Ripper. John the Ripper is a fast password cracker, primarily for cracking Unix (shadow) passwords.Other than Unix-type encrypted passwords it also supports cracking Windows LM hashes and many more with open source contributed patches. Jul 21, 2015 · Johnny the open source cross-platform GUI frontend for John the Ripper, the popular password cracker, written in C++ using the Qt framework. Johnny’s aim is to automate and simplify the password cracking routine on the Desktop as well as add extra functionality like session management and easy hash/password management, on top of the immense capabilities and features offered by …
Cracking Passwords with John the Ripper. This exercise complements material in the CompTIA Security+: Get Certified Get Ahead: SY0-501 Study Guide. Background. One of the methods of cracking a password is using a dictionary, or file filled with words. This lab demonstrates how John the Ripper uses a dictionary to crack passwords for Linux accounts. password generator and all-around cracking tool. John the Ripper · Category:John the Ripper. Installing John the Ripper on Kali 2.0: Kali 2.0/John the Ripper Testing John: John the Ripper/Benchmarking Using John on /etc/shadow files: John the Ripper/Shadow File. Password generation using rules and modes: John the Ripper/Password Generation Installing some useful password rules: John the
Cracking Passwords with John the Ripper. This exercise complements material in the CompTIA Security+: Get Certified Get Ahead: SY0-501 Study Guide. Background. One of the methods of cracking a password is using a dictionary, or file filled with words. This lab demonstrates how John the Ripper uses a dictionary to crack passwords for Linux accounts. Apr 19, 2019 · John The Ripper Password Cracking Tool Free Download (2019 Edition) In this guide, we learned about the password cracking software named “John the Ripper“. This tool is totally free to download and very good for password hacking and cracking. As I said before you should download the original version of this software because there are many
John The Ripper: Beginner's Tutorial John The Ripper: Beginner's Tutorial. In previous post on John The Ripper we saw how to compile it for Linux and UNIX boxes. Now its time to begin out password cracking journey with John The Ripper. Lab 8: Using John the Ripper to Crack Linux Passwords 3 This work by the National Information Security and Geospatial Technologies Consortium (NISGTC), and except where otherwise noted, is licensed under the Creative Commons Attribution 3.0 Unported License. Introduction
Cracking Passwords with John the Ripper. This exercise complements material in the CompTIA Security+: Get Certified Get Ahead: SY0-501 Study Guide. Background. One of the methods of cracking a password is using a dictionary, or file filled with words. This lab demonstrates how John the Ripper uses a dictionary to crack passwords for Linux accounts. John the Ripper password cracking tool - How to use Step by step guide IT Security. I will give 1min theory lec on this first :P John the Ripper is free open source password cracking tool for Linux , Unix and Mac OS X . A windows version is also available.
Beginners Guide for John the Ripper (Part 1) Hack News
Getting Started Cracking Password Hashes With John the Ripper. Dec 01, 2010 · By Thomas Wilhelm, ISSMP, CISSP, SCSECA, SCNA Many people are familiar with John the Ripper (JTR), a tool used to conduct brute force attacks against local passwords. The application itself is not difficult to understand or run… it is as simple as pointing JTR to a file containing encrypted hashes and leave it alone. In a professional penetration test, we don’t […], John the Ripper usage examples. These examples are to give you some tips on what John's features can be used for. Command line. 1. First, you need to get a copy of your password file. If your system uses shadow passwords, you may use John's "unshadow" utility to ….
How to Crack Passwords with pwdump3 and John the Ripper. Below a quick step-by-step guide on how to install and run the latest version of John the Ripper across several system using OpenMPI framework taking advantage of NFS to share common files. All this using Kali Linux. By creating this small environment we foster the knowledge and promote learning about different tools and techniques. The…, Dec 01, 2010 · By Thomas Wilhelm, ISSMP, CISSP, SCSECA, SCNA Many people are familiar with John the Ripper (JTR), a tool used to conduct brute force attacks against local passwords. The application itself is not difficult to understand or run… it is as simple as pointing JTR to a file containing encrypted hashes and leave it alone. In a professional penetration test, we don’t […].
Johnny GUI for John the Ripper [Openwall Community Wiki]
Step-by-Step Clustering John the Ripper on Kali Count. Dec 27, 2001 · Directed by John Eyres. With A.J. Cook, Bruce Payne, Ryan Northcott, Claire Keim. A massacre survivor (A.J. Cook) studies serial killers under a famous expert (Bruce Payne), but her classmates soon start dying at the hands of a Jack the Ripper copycat. https://en.wikipedia.org/wiki/Jack_the_Ripper_suspects May 21, 2019 · Hi I have a problem with John the ripper: Version :John the Ripper 1.8.0-jumbo-1 Windows XP SP3/ Windows 7 I tried to decrypt a winrar file but i....
We know the importance of John the ripper in penetration testing, as it is quite popular among password cracking tool. In this article, we are introducing the John the ripper and its various usage for beginners. What is John the Ripper? John the Ripper is a free password cracking software tool developed by Openwall. Originally developed for Unix Operating Systems but later on developed for John the Ripper password cracking tool - How to use Step by step guide IT Security. I will give 1min theory lec on this first :P John the Ripper is free open source password cracking tool for Linux , Unix and Mac OS X . A windows version is also available.
Below a quick step-by-step guide on how to install and run the latest version of John the Ripper across several system using OpenMPI framework taking advantage of NFS to share common files. All this using Kali Linux. By creating this small environment we foster the knowledge and promote learning about different tools and techniques. The… Jul 21, 2015 · Johnny the open source cross-platform GUI frontend for John the Ripper, the popular password cracker, written in C++ using the Qt framework. Johnny’s aim is to automate and simplify the password cracking routine on the Desktop as well as add extra functionality like session management and easy hash/password management, on top of the immense capabilities and features offered by …
Apr 02, 2016 · John the Ripper password cracker. John the Ripper – Cracking passwords and hashes John the Ripper is the good old password cracker that uses wordlists/dictionary to crack a given hash. Can crack many different types of hashes including MD5, SHA etc. It has free as well as paid password lists available. It is cross platform. password generator and all-around cracking tool. John the Ripper · Category:John the Ripper. Installing John the Ripper on Kali 2.0: Kali 2.0/John the Ripper Testing John: John the Ripper/Benchmarking Using John on /etc/shadow files: John the Ripper/Shadow File. Password generation using rules and modes: John the Ripper/Password Generation Installing some useful password rules: John the
John the Ripper is designed to be both feature-rich and fast. It combines several cracking modes in one program and is fully configurable for your particular needs (you can even define a custom cracking mode using the built-in compiler supporting a subset of C). Also, John is available for several different platforms which enables you to use If I know the mask of a password (a-z,A-Z,0-9, length 8 for example), how to teach john to try all mix? How to write a good wordlist to make it start trying? A step-by-step guide will be appreciated, I- have read many tutorial but still didn't find my exact issue. Thanks in advance.
Run ../run/john --test to make sure everything is OK Actually, some tests will likely fail because there are currently no "format destructors". you'd need to test the individual formats on their own, not all at once, to really make sure that everything is OK (or to find out if not, for real). Jul 12, 2015 · Home » Tutorials » John The Ripper – Kali Linux Tips and Cheats. Tutorials. John The Ripper – Kali Linux Tips and Cheats. by admin Published July 12, 2015. I created a quick reference guide for John the Ripper. Useful for those starting in order to get familiar with the command line. Print it, laminate it and start practicing your
Dec 27, 2001 · Directed by John Eyres. With A.J. Cook, Bruce Payne, Ryan Northcott, Claire Keim. A massacre survivor (A.J. Cook) studies serial killers under a famous expert (Bruce Payne), but her classmates soon start dying at the hands of a Jack the Ripper copycat. May 20, 2019 · Download John the Ripper. John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, and OpenVMS.
Feb 18, 2018 · Hey guys! HackerSploit here back again with another video, in this video, we will be looking at Linux and encrypted password cracking with John the Ripper. J... Dec 01, 2010 · By Thomas Wilhelm, ISSMP, CISSP, SCSECA, SCNA Many people are familiar with John the Ripper (JTR), a tool used to conduct brute force attacks against local passwords. The application itself is not difficult to understand or run… it is as simple as pointing JTR to a file containing encrypted hashes and leave it alone. In a professional penetration test, we don’t […]
John the Ripper. Next we’ll need the cracking tool itself. If you’re using Kali Linux, this tool is already installed. Download John the Ripper here. In my case I’m going to download the free version John the Ripper 1.8.0 (sources, tar.gz, 5.2 MB). Once downloaded, extract it with the following linux command: Feb 18, 2018 · Hey guys! HackerSploit here back again with another video, in this video, we will be looking at Linux and encrypted password cracking with John the Ripper. J...
Aug 08, 2013 · John the ripper is a popular dictionary based password cracking tool. It uses a wordlist full of passwords and then tries to crack a given password hash using each of the password from the wordlist. In other words its called brute force password cracking and is … Aug 04, 2011 · How to Install John The Ripper On Ubuntu Linux? -Works for All Linux. August 4, 2011 Ethical Hacking. This article will guide you how to install John The Ripper Tool(Password Cracker) in your ubuntu or Any other Linux and Unix Based System. Okay let us test whether John the ripper is …
john Package Description. John the Ripper is designed to be both feature-rich and fast. It combines several cracking modes in one program and is fully configurable for your particular needs (you can even define a custom cracking mode using the built-in compiler supporting a subset of C). John the Ripper is a free password cracking software tool. Initially developed for the Unix operating system, it now runs on fifteen different platforms (eleven of which are architecture-specific versions of Unix, DOS, Win32, BeOS, and OpenVMS).
How-to - Cracking ZIP and RAR protected files with John the Ripper Updated: 2014-07-31 3 minute read After seeing how to compile John the Ripper to use all your computer's processors now we can use it for some tasks that may be useful to digital forensic investigators: getting around passwords. Today we will focus on cracking passwords for ZIP and RAR archive files. Aug 04, 2011 · How to Install John The Ripper On Ubuntu Linux? -Works for All Linux. August 4, 2011 Ethical Hacking. This article will guide you how to install John The Ripper Tool(Password Cracker) in your ubuntu or Any other Linux and Unix Based System. Okay let us test whether John the ripper is …